BlockThreat - Week 22, 2024
DMM | Velocore | Orion | SCROLL | MetaDragon
Greetings!
This week, hundreds of millions of dollars worth of assets were stolen across seven incidents. We could do deep dives into a couple of very interesting exploits this week. However, it’s time to look at data and reassess how our industry has already lost more than $1B, with almost a third of losses occurring this month!
On the CeFi side, the massive $305M DMM exchange compromise sets us on track to exceed the $200M Mixin and $130M Poloniex hacks from last year So far, hot wallet compromises netted $353M to bad actors in 2024. Nation state and financial actors will continue using traditional exploitation techniques to target CeFi infrastructure. Techniques such as phishing, social engineering, credential stealing malware, and others are mostly well understood by these entities which have had more than a decade to either build their defenses or join the exchange graveyard.
The trend that alarms me the most is on the DeFi side. Here are the Top 10 exploitation vectors from first half of 2023:
As I discussed during my talk at last year’s DeFi Security Summit, most of the root causes behind the largest hacks were related to vulnerabilities in smart contracts and a lack of secure coding practices. Hacks due to price oracle or reward manipulation, weak function access controls, and various logic errors dominated the threat landscape. Operational security issues such as private key and governance management were a concern, but resulted in only about 1/4 of all losses.
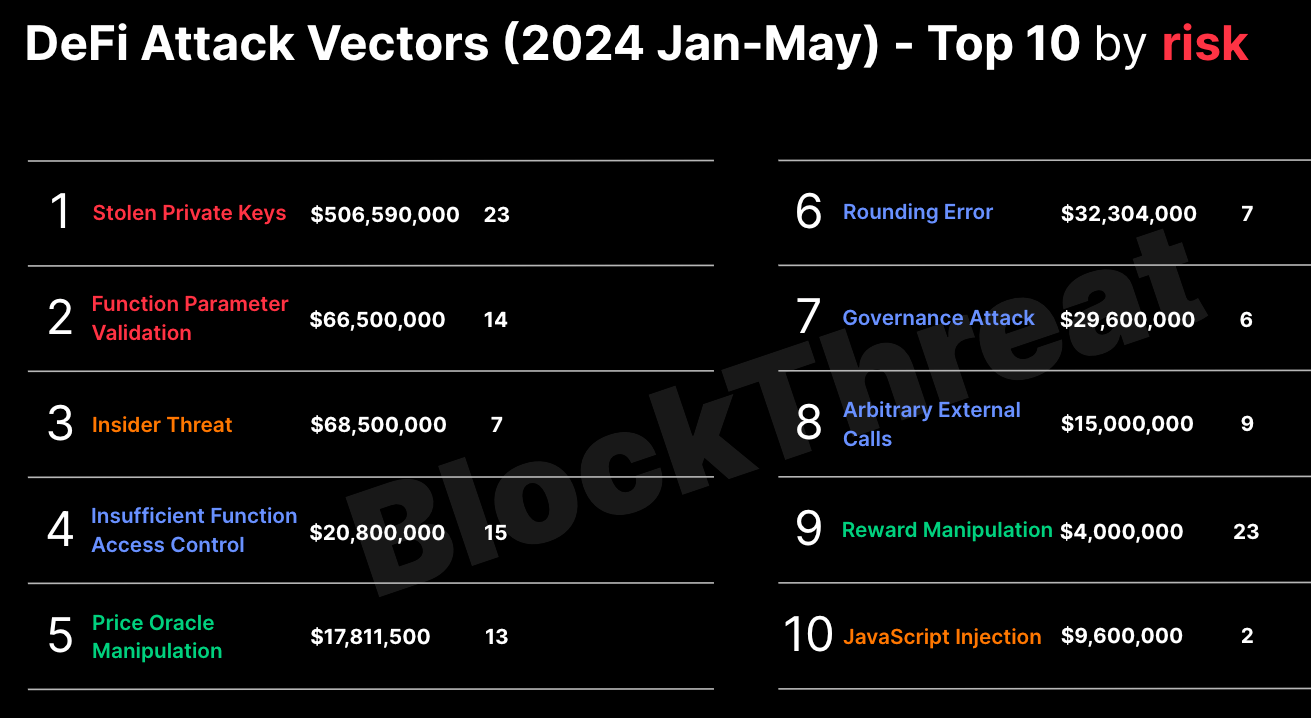
Fast forward to 2024, and the threat landscape has changed significantly:
On the positive side, price oracle and reward manipulation exploits are no longer resulting in as many losses. They were replaced by new smart contract exploitation vectors such as function parameter injection, rounding errors, and the embarrassing insufficient function access control weaknesses. However, it is the operation security related compromises such as stolen private keys, insider threat, governance, and back-end compromises that are now dominating the Top 10 DeFi Attack Vectors:
Secret management, insider threat, third party dependencies, cloud infrastructure, and others are all traditional security issues. We have been so focused on smart contract vulnerabilities that we have unfortunately neglected the rest of the threats.
Consider this an early warning. If you have been paying attention over the past few editions we already started covering interesting case studies and noting important lessons that go beyond smart contract vulnerabilities. Expect to see more coverage on insider threat, key management, infra security, threat actor profiles, DeFi security program building and related topics in upcoming editions.
However, don’t be too hard on yourselves. It’s also a sign of maturity. The ever evolving field of DeFi security is graduating from the initial code security/audit model into new domains such as security program management, security operations, threat intelligence, governance, insider threat, risk, compliance, and other frontiers. So whether you are just joining the field or a seasoned veteran, things are about to get very exciting.
As we celebrate the much overdue 5 year anniversary of the newsletter, I invite you to join me in this next chapter where we get to learn, explore, build, and hopefully make this industry a bit safer together. It’s worth it.
To gain access to comprehensive vulnerability write-ups, post-mortems, exploit proof of concepts (PoCs), attacker addresses, and additional data regarding this week’s compromises, please subscribe to the premium plan below.
Oh and be sure to check out Joe Grand’s latest hardware wallet exploit in the Media section. Let’s dive into the news!