BlockThreat - Week 22, 2025
Cork Protocol | Malda | Dexodus | Kidnappings
Greetings!
More than $12M was stolen this week across six incidents. The largest loss came from the Cork Protocol exploit, which featured a kill chain involving at least three well-known vulnerability classes including insufficient function access control and reward manipulation. The remaining incidents followed a similar pattern of more access control failures and price oracle manipulation.
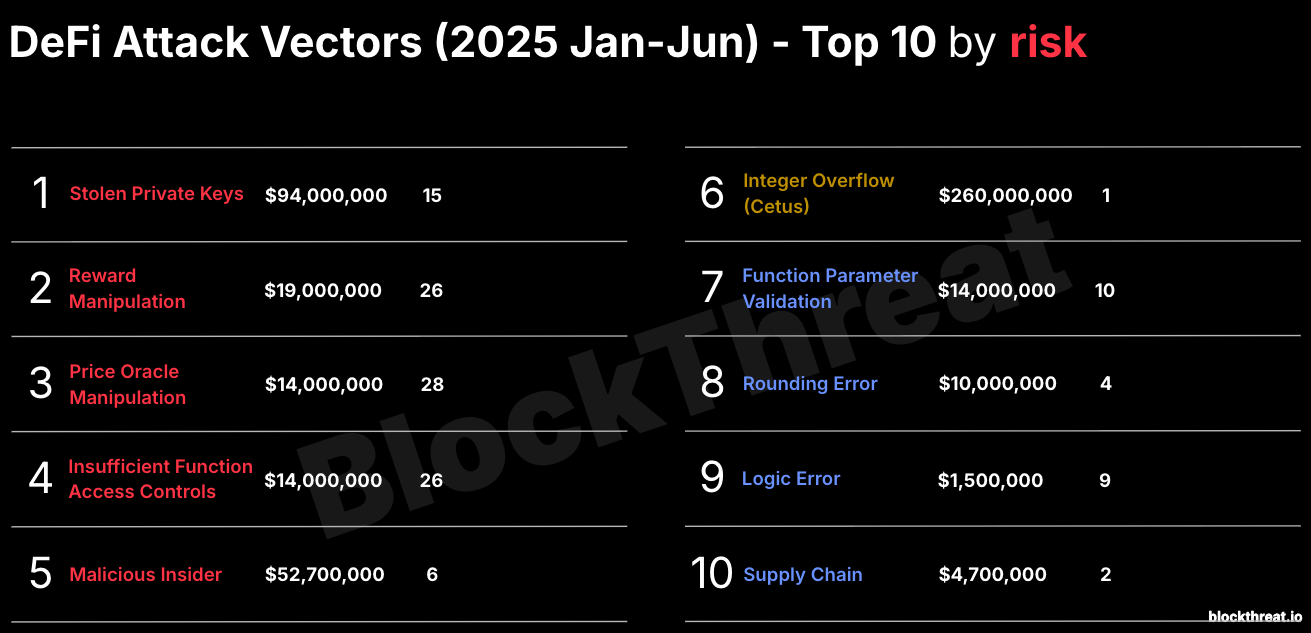
What’s becoming increasingly clear is that the same attack vectors keep resurfacing. These are not novel bugs. We should know them by now! So this week, I’m stepping back to highlight the Top 10 recurring attack vectors. Understanding these trends is essential to finally break the cycle of repeating the same mistakes.
Stolen private keys continue to top the charts. Addressing these operational security failures requires more than traditional code audits. Unfortunately, a holistic approach—one that includes analysis of both on-chain and off-chain components like endpoint security, cloud infrastructure, and key management—is still far from standard practice.
More concerning, however, is the rise of a deadly triad: Reward Manipulation, Price Oracle Manipulation, and Insufficient Function Access Controls. These three attack classes show up in the majority of high-impact incidents including this week’s $12M Cork Protocol exploit.
Notably, Reward Manipulation has clawed its way back into the #3 spot after a relative decline over the past year. This vector targets flawed incentive mechanisms, allowing attackers to extract protocol rewards such as fees, yield, or emissions without providing corresponding economic value or taking on real risk.
To help catch this vulnerability class consider adopting the following audit/code review practices and study respective case studies.
Verify that reward are proportional to economic contributions or risk (see Abracadabra Incident - $13M).
Simulate accounting logic behavior in various edge cases (see Euler Hack - $197M).
Trace every reward path and ensure that it can’t be manipulated (see Pickle Finance - $19.7M).
As in previous years, there’s always one standout hack that revives an attack vector we thought was mostly behind us. In 2025, it was Cetus on Sui that forced the industry to revisit the classic integer overflow—a bug class we haven't seen dominate in quite some time.
The rest of the Top 10 attack vectors remained largely consistent with prior years, with one notable exception: the appearance of the supply chain attack. This Web2-style operational security vector highlights the growing risks in our build and deployment pipelines. So please lock down your repos, audit your CI/CD workflows, and clean up your dependencies before attackers beat you to it.
Blockchain security demands staying constantly vigilant to emerging threats while prioritizing the most critical risks to address. I hope you will use the list above to build a safer and more resilient ecosystem.
Enjoy reading BlockThreat? Consider sponsoring the next edition or becoming a paid subscriber to unlock the premium section with detailed information on hacks, vulnerability, indicators, special reports, and searchable newsletter archives.
Let’s dive into the news!
News
FreeRomanStorm campaign needs donations to support the upcoming trial!
Inside the $400 million Coinbase breach: An Indian call center and teenage hackers. More details are revealed about TaskUs call center and threat actors behind the attack. According to the recent filing the breach dates back to December 26, 2024, but was only discovered on May 11, 2024.
Banking groups urge SEC to rescind Biden-era cybersecurity rule.
Someone loses over $500,000 in deUSD liquidation, raising concerns about Chainlink’s VWAP pricing system. Some debate ensued regarding the use of Chainlink oracles and low liquidity tokens. Time to check out Cyfrin’s excellent Chainlink Fundamentals course.
Solana’s Raj Gokal doxxed via Migos’ Instagram account after failed 40 BTC extortion bid.
Julia Garner and Anthony Boyle will portray Caroline Ellison and Sam Bankman-Fried in the new limited series The Altruists.
Crime
France charges 25 suspects in crypto abduction cases. Hopefully, this marks the end of the recent string of kidnappings in France.
Third Arrest Made in High-Profile Kidnapping of Bitcoin Investor in New York.
Stolen Crypto Traced: Ugandan Police Arrest Suspect in Blockchain Educator’s Abduction.
Russian national arrested in South Korea for attempted crypto robbery.
Crypto Up, Kidnapping Up? — Dissecting Cases from 2022 to 2025.
North Korea likely got Lazarus to work days after warship fiasco.
FBI Warns of Filipino Tech Company Running Sprawling Crypto Scams.
Interpol target ‘Madam Ngo’ arrested over $300M crypto scam.
Phishing
Not your seed = not your keys, a new ongoing attack where you could lose everything by Opsek.
Wintermute’s ‘CrimeEnjoyor’ to flag Ethereum’s wallet-draining contracts.
Top 7702 Delegator Revealed as Phishing Scam by GoPlus Security.
Dark Partner Hackers Using Fake AI, VPN & Crypto Sites to Attacks macOS & Windows Users.
Scams
MEXC exchange detects 200% surge in fraudulent activity in Q1.
Latam Insights: Milei Dissolves Libra’s Investigation, Colombian CBDC Comes out of Stealth.
LONG READ: How John Karony went from visionary to convicted fraudster.
Bubblemaps launches ‘Time Travel’ tool for insider activity, rug pulls.
Malware
A Wolf in Sheep’s Clothing: Analysis of the Osiris Malicious Browser Extension by SlowMist.
Dark Partners cybercrime gang fuels large-scale crypto heists.
Inside a VenomRAT Malware Campaign by DomainTools.
PumaBot: Novel Botnet Targeting IoT Surveillance Devices by Darktrace.
Hackers Exploiting Craft CMS Vulnerability To Inject Crypto Miner Malware.
New Self-Spreading Malware Infects Docker Containers to Mine Dero Cryptocurrency.
Media
bountyhunt3rz - Episode 15 - milotruck.
Ross Ulbricht's Speech at Bitcoin 2025. Ross received a $31.4M donation shortly after.
Contests
RethMatch - An onchain tournament for bots, inspired by Pac-Man and Agar.io.
Research
Enforcing Transaction Simulation Integrity: Pectra Edition by Bitfinding.
The Bug That Was Missed - How fuzzing for preconditions can lead to high severity vulnerabilities by Nican0r (Recon)
Riverguard: Mutation Rules for Finding Vulnerabilities by Sebastian and Thomas (Neodyme).
The Custodial Stablecoin Rekt Test by Benjamin Samuels (Trail of Bits).
Enterprise Crypto OpSec: A Comprehensive Guide for Companies by Three Sigma.
A Hitchhiker's Guide to Advance Solana Program Security by Accelerated Curve.
A deep dive into Axiom’s Halo2 circuits by Filipe Casal, Jim Miller, Fredrik Dahlgren, Joe Doyle, Tjaden Hess, Marc Ilunga (Trail of Bits).
Beyond Smart Contracts: A Deep Dive into Blockchain Infrastructure Security Auditing by Smriti Verma (OpenZeppelin).
Security Frameworks by SEAL - ENS Best Practices by Ghadi Mhawej (JustaLab)
Awesome Audits Checklists by ABDul Rehman (TheTradMod).
LLM-BSCVM: An LLM-Based Blockchain Smart Contract Vulnerability Management Framework.
A Systematic Classification of Vulnerabilities in MoveEVM Smart Contracts (MWC).
Tools
Sui Trace - Visualize token transfer patterns and track blockchain transactions with our advanced network graph.
Enjoy reading BlockThreat? Consider sponsoring the next edition or becoming a paid subscriber to unlock the premium section with detailed information on hacks, vulnerability, indicators, special reports, and searchable newsletter archives.