BlockThreat - Week 28, 2025
GMX | Kinto | Texture | Peapods | Pundai | Bankroll Network
Greetings!
More than $46M were stolen this week across seven incidents. We will focus on a sophisticated mass compromise followed by a whitehat recovery operation took place this week. For months, an unknown actor had been running scanners across multiple EVM chains, looking for new ERC1967Proxy contract deployments. If a proxy was deployed and left uninitialized, the attacker would quickly step in and initialize it first with a backdoor. The vulnerability itself was relatively simple, but the execution showed an impressive level of stealth and precision.
Let’s look at a case study involving one protocol affected by this campaign. On July 10, 2025, Kinto Protocol lost $1.55 million after the attacker upgraded the proxy to a backdoored implementation and minted K tokens. The exploit timeline is below:
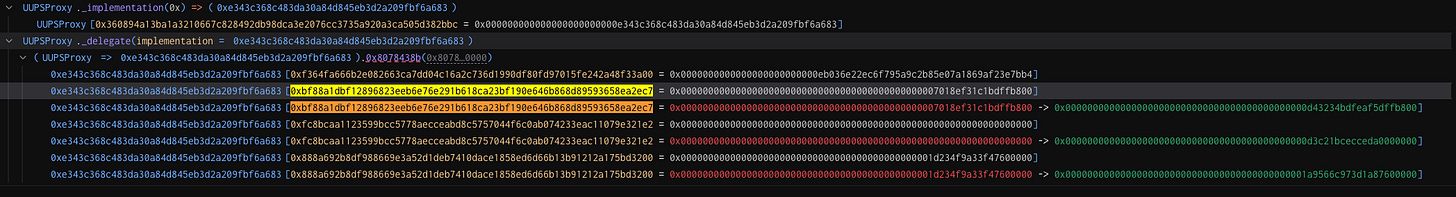
2025-03-19 20:24:40 - Kinto devs deploy the contract without initializing it(!) Implementation is set to 0x1a16bc [0x35d5fc]
2025-03-19 20:24:42 - Attacker initializes the contract with their admin account 0x2fc427. Implementation is set to the backdoor at 0x7382bc. All transactions will now pass through the backdoor to the decoy slot. [0xd17330]
2025-03-19 20:28:11 - Developers finish initialization with token name and their own admin account values. [0x1443ab]
2025-03-25 01:20:51 - Developers perform an upgrade. Implementation is now set to 0x7382bc. [0x18d7a5]
2025-07-10 08:33:11 - Exploit transaction to upgrade the decoy implementation to 0x3bcdf5 and backdoor implementation to 0xe343c3 while also updating storage slots for a few addresses to mint tokens [0x579f0d].
2025-07-10 08:33:32 - First illicit transfer to 0xde86b4 [0x07f516].
2025-07-10 08:33:40 - Starting to drain the Morpho vault [0x4635f0].
2025-07-15 12:12:16 - Attackers upgrade the contract with new implementation 0x25d1f4 to include ransom logic [0x178dcd].
2025-07-15 12:18:22 - Attackers sent a ransom offer to recover contract implementation address by sending 5 ETH. That’s a new one! [0x552fd2]
The backdoor was cleverly designed to survive reinitialization and multiple upgrades, lying dormant until the day the attackers finally decided to pull the trigger. I’ll leave the deep-dive analysis of the compromise to the reader using the resources above. Instead, I want to focus on what makes this exploit both uniquely sophisticated and particularly malicious.
Some of the stealth techniques used:
The attackers carefully reset all initialized parameters and storage in the victim contracts, while preserving pointers to the original implementation contracts to make everything appear untouched.
As noted by pcaversaccio, the attacker exploited a zero-day in the Etherscan family of blockchain explorers, spoofing the implementation by layering an OpenZeppelin proxy on top of an EIP-1967 proxy and the backdoor itself. Three proxies stacked in one.
Rather than triggering a noisy mint() function, the attacker wrote tokens directly into storage slots tied to fake addresses.
Vault draining was done rapidly but in small increments
The operation was active for months, likely waiting for the juiciest target or perhaps preparing to drain all victims at once. All the infrastructure needed for extraction was in place well in advance.
We are dealing with a highly advanced threat actor with deep knowledge of proxy patterns, EVM storage mechanics, and the ability to drop zero-days in critical on-chain infrastructure. According to deebeez, thousands of smart contracts were compromised with over $10M at risk.
That brings us to the second half of this story, one that reminds me why this community is so special and why I keep coming back week after week to research and document its history. deebeez and the team at VennBuild discovered the vulnerability before widespread damage occurred and quickly partnered with pcaversaccio, Dedaub, and the SEAL 911 team to launch a 36-hour war room, reaching out to vulnerable projects and recovering most of the funds at risk. A few were unfortunately missed, but the outcome could have been far worse. Hurray!
Some lessons learned from this incident:
I’m noticing an alarming rise in ecosystem-wide incidents. We got lucky this time, but it feels like a far more devastating event could be just around the corner. Stay vigilant and pay attention to emerging attack vectors.
Always use atomic create-and-initialize transactions when deploying proxies. Doing so would have prevented this mass exploitation from happening in the first place.
Do not rely solely on public infrastructure like blockchain explorers. Always verify state independently by querying the blockchain directly using automated tests or tools such as cast.
Similarly understand the limits of blockchain detection and alerting. Simple transaction or log monitoring is no longer sufficient. For example, attackers easily bypassed monitors for admin functions like minting by modifying storage slots directly. Instead focus on invariant detection (e.g. pool value dropped, total supply increase beyond expected, etc.)
Attackers are exploring new ways to profit by now building ransom logic into compromised contracts. I’ve never seen anything like this before!
Despite some of the notes, this threat actor’s TTPs really don’t look like DPRK.
Speaking of good security advice, check out this week’s sponsor and get your protocols audited before disaster strikes.
Oak Security has operated in Web3 Security since 2017, providing security services throughout a project's lifecycle. This includes audits, penetration testing, operational security training, and advisory services. Our signature blinded process emphasises redundancy: Every line of code is reviewed by multiple auditors with a multi-disciplinary background in parallel.
Link: https://www.oaksecurity.io/
In other news attackers returned combined almost $40M in stolen assets from GMX and Texture hacks this week after taking the usual “bounty”. We also learned about a whitehat recovery and a responsible disclosure of a reentrancy vulnerability in Cove from about a month ago. No ransom or endless negotiations about the “bounty” size, just a bug bounty program working as it should.
Enjoy reading BlockThreat? Consider sponsoring the next edition or becoming a paid subscriber to unlock the premium section with detailed information on hacks, vulnerabilities, indicators, special reports, and searchable newsletter archives.
Let’s dive into the news!
News
The CPIMP Attack: an insanely far-reaching vulnerability, successfully mitigated by Dedaub. A deep dive into the whitehat operation described above which helped save more than $10M from a mass backdooring of proxy contracts.
Bitcoin Depot breach exposes data of nearly 27,000 crypto users. It took more than a year to report the hack from 2024.
CVE-2025-48384: Breaking Git with a carriage return and cloning RCE. Recursive cloning on an untrusted repo can lead to code execution. This will likely appear in future “fake job” phishing campaigns.
Builders are engaging in MEV. Analysis of an ongoing issue on BNB Chain by Tommyhom.
Crime
Following the Frozen: An On-Chain Analysis of USDT Blacklisting and Its Links to Terrorist Financing by BlockSec.
Following the money: How the SDNY caught the Crema hacker. Timing attacks and bad opsec is the downfall of amateur criminals.
Russian Hosting Provider Aeza Group Sanctioned for Aiding Hackers and Darknet Drug Markets by Lisa and Liz (SlowMist).
Sanctions Imposed on DPRK IT Workers Generating Revenue for the Kim Regime.
Policy
Phishing
The Phishing Dojo by The Red Guild. A threat simulation platform designed to help crypto users identify and defend against social engineering, phishing, scams, and other notorious threats in the crypto ecosystem.
The official X account of Plasma has been compromised.
Malicious pull request infects VS Code extension by Petar Kirhmajer, Threat Researcher (ReversingLabs). ETHCode extension is used by many crypto developers. The malicious PR included a new package keythereum-utils which downloads a secondary payload in an apparent supply chain attack.
Code highlighting with Cursor AI for $500,000 by Kaspersky. Similar to above, a malicious Solidity VS Code extension was used to steal private keys from a developer. Note that the package appeared in the Open VSX registry used by Cursor AI while the official VS Code repo flagged it immediately.
The obfuscation game: MUT-9332 targets Solidity developers via malicious VS Code extensions by Datadog Security Labs.
Scams
When Crypto Market Makers Lose Trust: From Blind Faith to Institutional-Grade Scrutiny by Nefture Security.
Telegram Purged Chinese Crypto Scam Markets—Then Watched as They Rebuilt by Andy Greenberg (Wired).
Malware
Crypto Wallets Continue to be Drained in Elaborate Social Media Scam by Darktrace. Users are targeted with malicious meeting software from fake gaming and AI companies over Telegram and Discord.
New North Korean malware targets crypto startups via fake Zoom invites by Ray Fernandez (Moonlock).
Taking SHELLTER: a commercial evasion framework abused in-the-wild by Seth Goodwin, Daniel Stepanic, Jia Yu Chan, Samir Bousseaden (Elastic Security Labs).
OtterCookie: Analysis of Lazarus Group Malware Targeting Finance and Tech Professionals by Any Run.
Media
bountyhunt3rz - Episode 20 - chasethelight.
Indexed Podcast - Is EIP7702 a double edged sword? featuring FrankResearcher talking about security implications of the recent upgrade.
Ledger CTO | Charles Guillemet with Patrick Collins on wallet security.
Crypto K1ds - Upcoming Netflix documentary about the $240M Malone Lam heist.
Research
Labubu: Toy Story Gone Wrong by Clarity Alliance. A deep dive into ALEX lab compromise on Stacks back in June.
Unveiling Access Control in Ethereum Smart Contracts: Common Access Control Vulnerabilities by Alice Hsu.
Real AI Agents with Fake Memories: Fatal Context Manipulation Attacks on Web3 Agents.
LLM-Driven Blockchain Security Products: From Practice to Theory — A Preliminary Discourse by Nerbonic.
Can you trust a DeFAI agent? by QuillAudits.
Deep Mental Models for Solidity ABI Encoding: Part 2 by Zaryab Afser.
Static Analysis for Detecting Transaction Conflicts in Ethereum Smart Contracts.
ETrace:Event-Driven Vulnerability Detection in Smart Contracts via LLM-Based Trace Analysis.
VERITE dataset and the Smart Contract Fuzzing Towards Profitable Vulnerabilities paper.
Post Contract Deployment Checklist by shafu.
Contests
Blockchain Bridge Vulnerabilities by The Caliber.
Tools
Bastet - a comprehensive dataset of common smart contract vulnerabilities in DeFi along with an AI-driven automated detection process to enhance vulnerability detection accuracy and optimize security lifecycle management.
HyperIndex - fast, developer-friendly multichain indexer, optimized for both local development and reliable hosted deployment. It empowers developers to effortlessly build robust backends for blockchain applications.Developed by Envio.
Investigate your dependencies with Deptective by Trail of Bits.
Picus is an implementation of the QED2 tool, which checks the uniqueness property (under-constrained signals) of ZKP circuits.
Enjoy reading BlockThreat? Consider sponsoring the next edition or becoming a paid subscriber to unlock the premium section with detailed information on hacks, vulnerabilities, indicators, special reports, and searchable newsletter archives.