BlockThreat - Week 44, 2024
LottiFiles | 1inch | M2 | MetaWin | Sunray
Greetings!
This week’s compromises were dominated by operational security issues, including supply chain attacks, private key theft, hot wallet drains, and social engineering.
The LottieFiles library supply chain attack was particularly noteworthy because it clearly targeted the cryptocurrency industry by injecting a drainer into all DeFi applications using this third-party library. Only 1inch publicly identified itself as a victim, but it’s likely there are many others. Front-end compromises are rare and are typically caught quickly by vigilant users. Similar incidents, such as Velvet Capital, Spooky, and others were all caused by reliance on external code that was included in their front-ends. This attack vector could be mitigated by freezing and self-hosting any external code while implementing a code review process for any updates or additions.
The rest of the compromises were massive hot wallet hacks such as the M2 Exchange ($13.7M) and MetaWin ($4M) hacks, as well as a private key theft that enabled infinite token minting on Sunray Finance ($2.8M). You can find detailed writeups and indicators in the premium section below.
To gain access to comprehensive vulnerability write-ups, post-mortems, exploit proof of concepts (PoCs), attacker addresses, and additional data regarding this week’s compromises, please subscribe to the premium plan below.
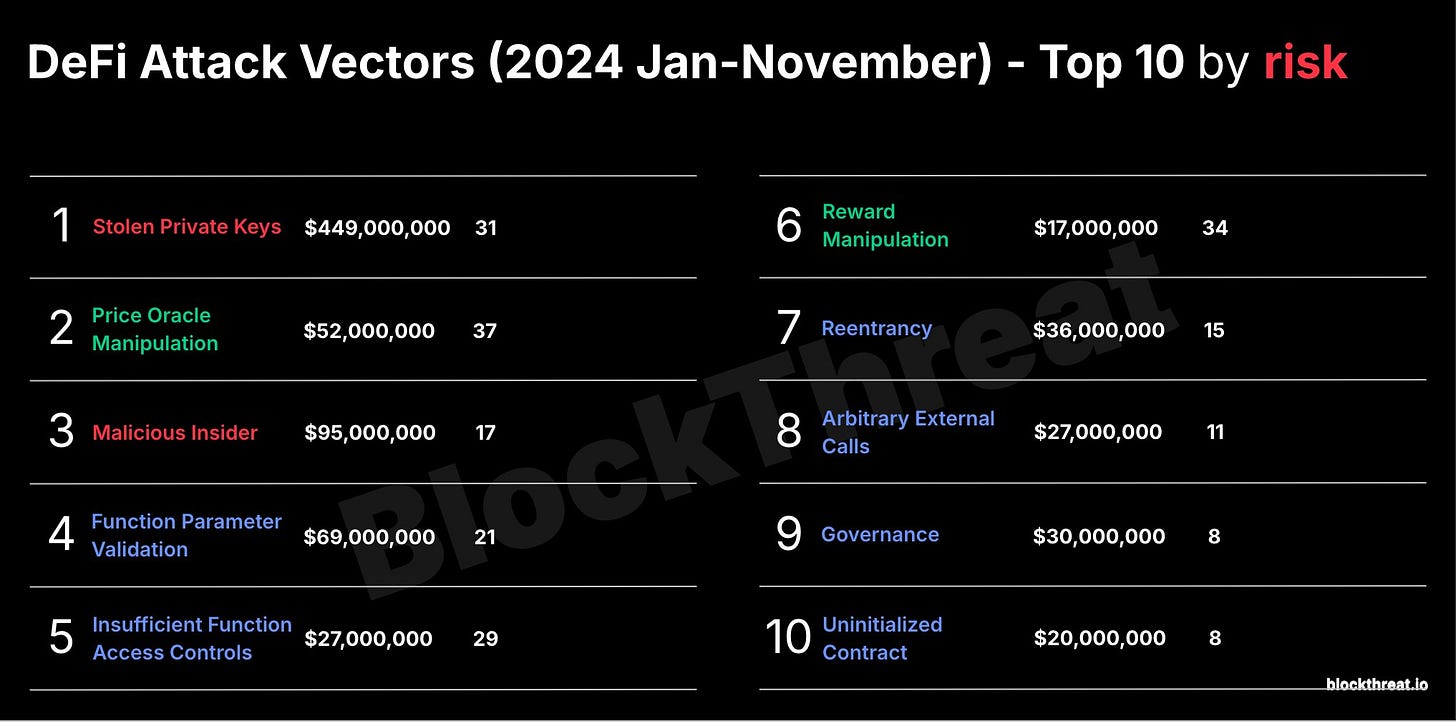
Notably absent were hacks caused by smart contract exploitation. I had an opportunity to discuss this trend during my State of DeFi Security talk at DSS. Here are the Top 10 attack vectors plaguing the DeFi ecosystem:
Notice how the Stolen Private Keys vector significantly outweighs all others. When such exploits occur, we often lack a full understanding of the entire kill chain since much of the hack happens off-chain. Hidden within this off-chain fog are traditional security issues and exploitation methods, ranging from phishing to infrastructure hacks. As an industry, we must intensify our efforts to protect our projects.
Let’s dive into the news!